-1200.webp)

Seamless IT management ensures that your technology infrastructure operates smoothly and efficiently, minimizing disruptions and maximizing productivity.

Our services are tailored to meet the unique needs of startups and growing businesses, providing scalable IT solutions that evolve with your company.
.svg)
Our US-based team offers IT solutions that extend globally, ensuring your business receives top-tier support no matter where you operate.
.png)
.svg)

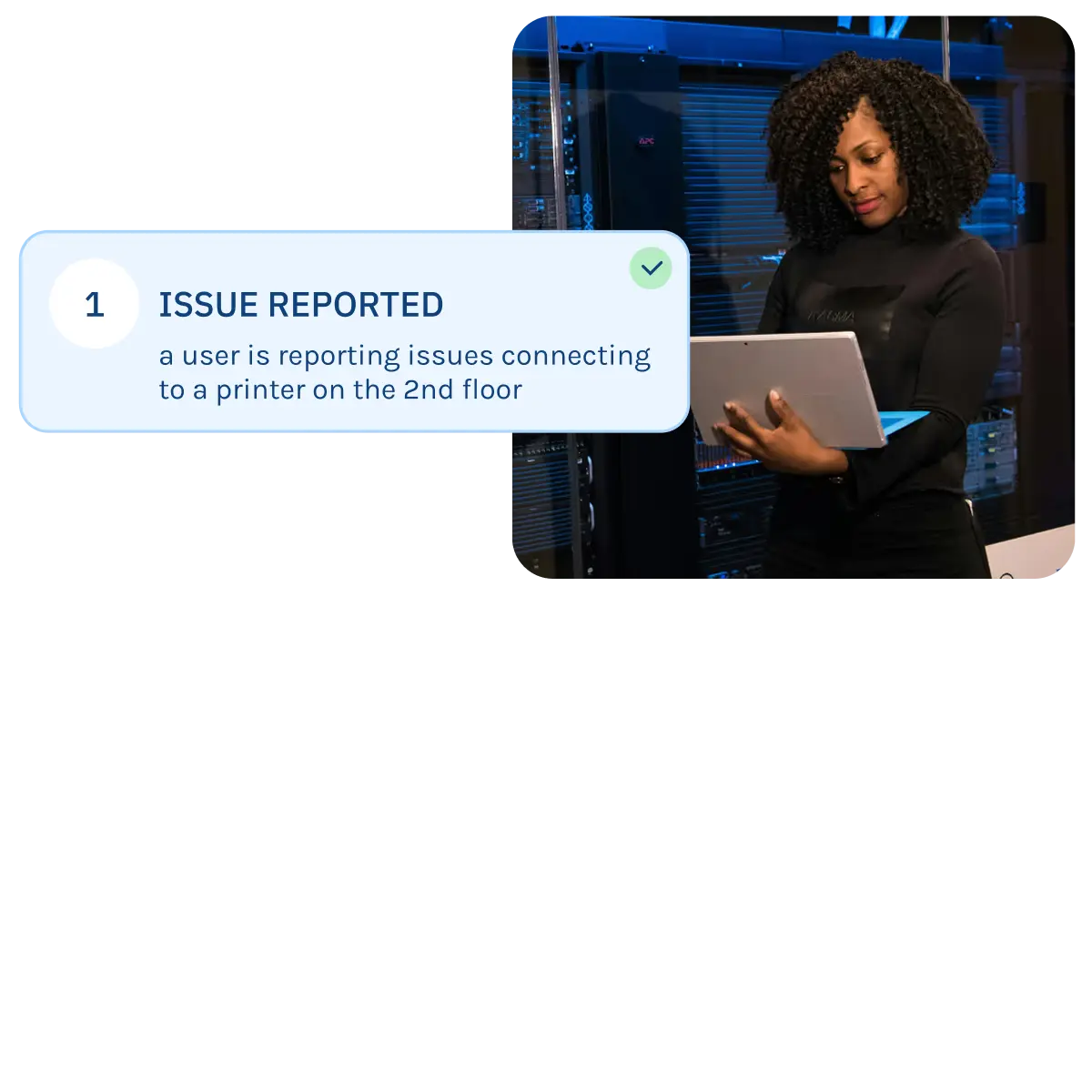



.svg)
.svg)

.svg)

.svg)


.svg)
.svg)

.svg)
.svg)
.svg)
.svg)


.svg)
.svg)
.svg)