Find expert perspectives that help you move forward with confidence.
Empowering IT Support to Deliver Efficiency, Reliability, and Satisfaction Across Every Interaction
June 9, 2025


July 11, 2025
In an AI-saturated landscape, the question isn’t whether machines can handle IT tasks, it’s when they should, where they fall short, and how to maximize both automation and human insight.
For many companies, AI-powered platforms promise speed and savings by automating routine workflows. That’s a powerful value, especially when your team is lean or growing fast. But IT doesn’t exist in a vacuum. It sits at the intersection of people, systems and priorities. That’s where a human-first IT partner like Network Right comes in to guide AI.
We believe the future of IT isn’t one-size-fits-all automation. It’s a co-pilot model, where AI handles the routine, while our human-led team brings the strategy and expertise to move your business forward.
Human-first IT doesn’t mean resisting innovation. It means recognizing that people (not platforms) are the backbone of effective, reliable IT. In today’s AI-saturated landscape, this model is more important than ever.
AI may recognize patterns, but it takes a human to understand context. Whether it’s navigating undocumented systems, resolving user frustration, or balancing shifting dynamics inside your organization, people adapt in ways automation can't.
Human IT pros bring intuition, creativity, and lived experience to problems that don’t have a script.
When your CEO is locked out of his computer before a board meeting, what are you going to do in crisis mode? You reach out to the friendly faces of IT.
This is where the human connection makes all the difference. By bridging the gap between technical know-how and human understanding, IT professionals build relationships rooted in trust and empathy. This foundation not only instills confidence across teams, but cultivates resilience, empowering everyone involved to overcome challenges together, no matter how unexpected.
The best IT leaders are more like trusted advisors than troubleshooters. That’s by design.
Humans don’t just implement technology, instead they can align it with the long-term vision, ask “why” behind every request, and help see the business impact beyond the tech stack.
Human-first IT doesn’t overlook AI. In fact, it often relies on it quietly in the background to flag issues and streamline processes. But the decisions and strategic insight? That’s still where people shine.
AI tools excel at managing IT workflows, especially for small, repetitive tasks. This AI-only approach can efficiently handle routine operations that require reliability over complexity, offering short-term relief. Their effectiveness is highest when tasks are clear and environments predictable, with known variables and straightforward outcomes.
Tasks such as resetting passwords, provisioning standard software packages, and enforcing access policies are typically low-risk and ideal candidates for automation. These processes follow clear rules and require little-to-no (human) judgement.
When a task is repetitive and well-documented, AI agents can usually handle it with no problems reducing the burden on IT teams but also helps ensure a reliable user experience.
When the main IT support you need is for around-the-clock monitoring and scanning logs, spotting unusual patterns in usage, and detecting common security threats then an AI-first solution can be your primary support.
However, while AI can raise the flag when something looks off, it still takes a human to evaluate the context and choose the appropriate response.
So even in these seemingly “safe” scenarios, AI still needs a human to loop in for guidance; someone to validate, fine-tune, and ensure outputs don’t introduce risk. AI is incredibly capable but it’s not infallible. At best, it is a proactive assistant. Not the pilot.
The most effective IT strategies today don’t force a choice between AI and people. Instead, they integrate both, allowing each to contribute its strengths. The complementary pair work hand in hand to bring speed, consistency, accuracy, empathy, and strategic vision. When these capabilities are combined with intention, the result is an IT team that scales effectively, adapts quickly, and builds trust over time.
AI agents trained on internal IT documentation can quickly perform initial troubleshooting, resolving common issues or pointing users in the right direction before escalating to senior technicians. This significantly reduces the volume of routine tasks, allowing skilled staff to focus on complex challenges.
AI tools can rapidly analyze large sets of logs, pinpointing errors and anomalies faster than manual inspection. This proactive approach accelerates resolution time and helps prevent issues from escalating into critical problems. As a lean team, AI agents function as a reliable digital teammate that is always on, fast, and efficient.
AI tools are evolving. With tools like Scribe and Warp, it’s never been faster or easier to build comprehensive documentation and how-to guides for your scripts or tools.
Ultimately, incorporating AI into IT workflows provides teams with a reliable partner capable of efficiently handling many routine tasks. The co-pilot model ensures you're covered across automation and insight, and allows experienced team members to focus their expertise on validation, refinement, and strategic oversight, in order to create balanced and effective collaboration.
At Network Right, we've built our IT systems around this principle to unite human insight with AI capabilities to proactively shape change rather than merely react to it. Our approach isn't about choosing between people or agents; it's about pairing them thoughtfully to create dependable IT solutions that evolve alongside your business.
AI is changing IT for the better, but only when guided by people who understand the nuances behind tickets, systems, and stakeholders. The most effective approach isn’t automation alone—it’s partnership.
At Network Right, we believe human-led IT is the foundation of business continuity and security. When paired with the right AI tools, it becomes a powerful force for growth.
So if you’re thinking about how to support a fast-growing team, improve your IT operations, or simply make sure nothing slips through the cracks, we’re here to help you lead with people, and power up with AI.
Ready for smarter, human-first IT? Let’s talk.

June 16, 2025
As we companies slowly begin to transition back to partial employees in the office be it by percentage, department, etc. There are several factors to keep in mind from the IT side of the house when it comes to returning to the office. After a year of adapting to mostly remote work, there are some items on the checklist to help ensure your best prepared for the hybrid workplace.
All of which we at Network Right have and are in the process of helping our clientele assure are up to date as the shift begins.
Given that many office conference rooms have been decommissioned for quite some time there a few things to have your team confirm prior to having employees working out of the office again.
Part of what makes a great conference room is access to common IT adapters & cables such as chargers, HDMI cords, and so on. Making sure prior to return that these are all available will make the transition that much more smoother.
Amidst the pandemic many look to save costs where they could & software such as conference room were one where people may have either not renewed or paused until they were back in office. It’s worth in the switch a hybrid setup you validate all licenses are good to go. Additionally it may be worth at least only activating some conference rooms dependent on your head count. That way your not overpaying for unused rooms but still have a sufficient amount to serve the employees who will be back to office.

Similar to the previous mentioned tip its worth re-evaluating your software spend as the transition to a hybrid space begins. Certain employees for example will certainly still need your Zoom accounts while others who will be fully onsite may not due to the Zoom Room/Conferencing setup. This is where you can do a break down & audit any software or licenses bought during the work-from-home/remote switch & determine which parties or departments need to retain said application access.
Some tools were super useful & great while everyone was remote where as new solutions or less licenses/seats will be needed now with people shifting back to office.
Other examples can include:

As employees come back to the office one key aspect to check on will be the network. Ensuring all services are still operational in event you cancelled any prior (ISP, Hardware subscription, etc). Also doing some prior checks to ensure things like network firmware for access points, routers, firewalls are all up to date for safety/security as well as efficiency for your workforce.
Small tips such as:
In some cases we even advise depending on the growth/scale of a company over the 2020 pandemic year to potentially re-evaluating your network setup.
An use case we can provide as example would be we have had clients who prior to the pandemic had a network setup better suited for a smaller sized companies and at their previous headcount. However scaling over the last year to 30+ more employees and expanding their space internally meant they needed more AP’s to cover the bigger space and headcount. Currently with offices closed or little to no one working out of them is the best time to perform any hardware upgrades or setups. That way everything is prepped & ready as people return.

A big part of the hybrid setup will revolve around users alternating around onsite & remote presence. As such some companies are looking into hotel desk options. These provide employees a temporary station they can book when their in office for days at a time or even remote employees visiting another office location. Hotel desks offer basic equipment that any team member can come in & connect to with ease.
We advise the following when it comes to offer flex/hotel desks.
This is a great way to offer space to work for employees who may only come in from time to time especially with current limitations that may be in place.

Lastly in this transition to both onsite + remote. It’s a perfect opportunity for IT to ensure inventory of important hardware laptops, mobile devices, and so on are all up to date. One big challenge in the remote shift was ensuring IT teams could easily keep track of hardware both new and old as companies onboarded in the remote times. At Network Right we rolled out solutions such as mobile device management or MDM to log devices & easily keep track.
That said as employees come back to the space some of which may have been onboarded amidst the pandemic will need new hardware keyboards, mice, monitors and so on. This is a great opportunity to ensure inventory is checked & that IT has a good sense of what is available for employees & what needs to be re-stocked. Guaranteeing hardware availability as waves of employees return to office.
Overall we know the transition won’t happen all at once or even at all for some. However, the hybrid workforce is something to consider amidst these times & preparing now on the IT side of things only helps your team & provides a better experience for the employees. Using the above list to make sure your infrastructure is prepped, audited, and updated to support the times ahead.
If your company has any inquiries or interest in the above-mentioned tips to ensure your office & team are set for the hybrid transition don’t hesitate to reach out to hello@networkright.io to see how we can help!

June 16, 2025
Having an extensive network of software and hardware partners and service providers is the way to go if you want to boost your business’s tech capabilities.
Collaborating with a wide array of partners broadens your technological horizons and enhances your competitive edge. Such a network provides access to specialized skills and innovative technologies that can be tailored to meet your unique business needs on demand.
However, the challenge lies in identifying which partnerships will most effectively propel your business forward.
Essentially, how do you select the right partners to not just meet but exceed your strategic goals?
Before diving into partnerships, you must clearly identify your business’s specific software and hardware needs.
Below are some crucial points to consider:
Forming strategic partnerships allows you to leverage external expertise and technology to enhance your business’s operational efficiency and innovation. Think of it as an avenue to share resources, multiply your capabilities, and achieve goals that are difficult to meet on your own.
The right partnerships breathe new life into your operations, allowing you to expand into new markets and refine your products with insights you mightn’t have internally.
Consider the emotional and practical impacts these partnerships can create:
These partnerships aren’t just beneficial—they’re transformative, setting you on a path to sustainable growth and success.
To effectively map the partner landscape, you’ll need to identify potential allies whose capabilities complement your business objectives.
First, pinpoint the specific needs of your business that require external support, be it advanced software solutions, hardware systems, or both. Understanding the nature and scope of your needs helps filter through the many available options.
Then, segment the potential partners into categories based on their offerings. For example, categorize them into software developers, hardware manufacturers, and integrated solution providers. This segmentation allows you to view the landscape more systematically and identify overlaps and gaps in the market offerings.
You should also consider geographical considerations. Are you looking for partners located nearby for ease of coordination, or is your search global, aiming to tap into the best worldwide? Mapping out the locations of potential partners helps you understand logistical dynamics that could affect your decision.
When evaluating potential software and hardware partners, you’ll need to take into account their expertise first. Check how compatible their products are with your current systems and what kind of integration efforts are required.
You should also inquire about their support and maintenance commitments to guarantee ongoing reliability.
Evaluating a partner’s expertise guarantees you’re aligning with skilled professionals who can meet your business objectives effectively. You need partners who not only understand their industry but also excel in it. Here’s how to make sure you’re choosing the best:
Choosing wisely will elevate your business, promoting progress and innovation.
Evaluating potential partners’ compatibility is essential for ensuring seamless operations and synergy in your business ventures.
Assess whether their software can easily communicate with your existing systems. Look beyond the technical specs; determine if their tools can adapt to your workflows and enhance your team’s efficiency.
Ask potential partners about APIs, data exchange protocols, and customization capabilities. You want to make sure they can integrate smoothly without causing disruptions or requiring expensive overhauls.
It’s also wise to look into user interfaces. If a tool is difficult to use, its integration won’t matter. Find a balance between functionality and user-friendliness to really leverage your new partnerships.
Evaluating a partner’s support and maintenance commitments is essential to ensure they can promptly address any issues and provide ongoing enhancements.
Here are key factors to consider:
Choose a partner who stands firmly beside you, not just on paper, but in action and commitment.
Your network should be positioned to reach and interact with industry leaders in relevant fields.
To effectively engage with industry leaders, you’ll need to:
Ultimately, engaging with industry leaders is as much about making a sale as it is about forming strategic relationships that foster long-term collaboration and growth. Keep your approach focused and adaptive, and you’ll be in a better position to connect with the upper echelons of your industry.
Businesses looking to make a headway in their industry must make thoughtful attempts to leverage partner ecosystems. This will position them to enhance their product capabilities and also expand their market reach.
Collaborating with the right partners opens the doors for you to tap into new networks and technologies that propel your business forward.
This strategic approach allows you to offer more all-encompassing solutions to your customers, setting you apart in the competitive landscape.
Tapping into partner ecosystems can greatly broaden your market reach and boost your business’s visibility. By aligning with the right partners, you’re not just sharing resources; you’re also tapping into their customer base, which can exponentially increase your own. It’s a strategic move that can lead to impressive growth and new opportunities.
Here’s how impactful this collaboration can be:
These partnerships aren’t just practical; they resonate on a deeper level, driving your business forward with shared success.
Building on expanded market reach, leveraging partner ecosystems can also greatly enhance your product capabilities.
By collaborating with a diverse array of software and hardware providers, you’re not just accessing new technologies; you’re integrating cutting-edge solutions that can differentiate your products in the market. This will help you optimize your IT ecosystem with right software and hardware solutions.
For clarity: your partners’ expertise allows you to innovate faster and more effectively, turning standard offerings into customized solutions that meet specific customer needs.
This strategy will enhance the overall value of your products. From improved performance to advanced functionalities, the input from your partners can lead to significant product enhancements.
Hence, you’ll be able to keep up with industry trends and even stay ahead in most scenarios, ensuring your business remains competitive and relevant.
To effectively customize solutions, you must first clearly understand your specific business requirements and objectives.
Once you’ve got a firm grasp on what you need, the next step is selecting the right software and hardware partners who can tailor their offerings to match your vision. The goal should be to find a partner who will work with you to craft a solution that meets and exceeds your expectations.
Here’s why customizing solutions specifically for your business can make a significant difference:
Understanding partnership agreements requires you to carefully assess terms that align with your business goals and protect your interests. When entering into partnerships, especially with software and hardware providers, it’s essential that you grasp every clause.
Don’t hesitate to negotiate terms that don’t sit well with you. Remember, clarity in these agreements prevents misunderstandings and potential legal conflicts down the line.
Ensure you’re clear on the scope of the partnership. What exactly are your partners providing, and what are your responsibilities? This clarity will help you manage expectations and deliver on your commitments. Pay particular attention to the duration of the agreement. Is it a one-time collaboration or an ongoing partnership? This affects how you plan your resources and business strategies.
You should also understand the exit strategies and any penalties associated with breaking the agreement. Sometimes, things don’t work out, and it’s better to have an amicable method to part ways than to be caught in a costly legal battle.
Finally, always have legal counsel review the documents. Their expertise can pinpoint potential issues that you might overlook.
Assessing partnership agreements isn’t just a formality—it’s a safeguard for your business’s future. Be diligent, be aware, and choose partners who reflect your business values and goals.
As you explore integrating new technologies into your business, it’s important to select technologies that align with your specific needs.
You’ll face challenges during implementation, but understanding these hurdles can help you overcome them effectively.
The technologies you use often determine how effectively your business integrates and benefits from new advancements. It’s important to make informed choices that align with your current business model and propel you toward future growth.
Here’s how you can guarantee you’re on the right path:
Once you’ve chosen the right technologies, you might face some challenges when integrating them into your operations. It’s essential to prepare your team for the changes ahead.
Start with training sessions that familiarize everyone with the new systems. You’ll need to manage expectations by setting realistic goals and timelines. It’s common to encounter resistance from staff, so proactive communication is key. Explain the benefits and how the technology will make their work easier in the long run.
Additionally, prepare for technical hiccups. Have a dedicated support team ready to handle queries and solve problems quickly. They’ll be your frontline in ensuring that the implementation doesn’t stall. Remember, patience and preparedness are your best tools here.
To guarantee the smooth integration of new technologies, you’ll need to carefully plan the shift and actively involve all stakeholders. It’s important that everyone’s on board and understands the changes ahead.
Here’s how you can make this shift as seamless as possible:
Building and maintaining long-term collaborations with software and hardware partners can greatly enhance your business’s growth and innovation. To sustain these relationships, you’ll need to focus on clear communication, mutual benefits, and regular engagement.
First, guarantee that communication lines are always open. You’ve got to be proactive in sharing updates, challenges, and feedback. Remember, it’s not just about airing your needs but also listening to your partners’ concerns and suggestions.
Secondly, emphasize creating mutually beneficial arrangements. You have to bring something to the table too. Whether it’s shared resources, joint marketing efforts, or collaborative product development, make sure there’s value for both sides.
Lastly, keep the relationship dynamic and engaging by regularly reviewing the partnership terms and exploring new areas of collaboration. Don’t let your connections stagnate; innovation comes from continual engagement and brainstorming new ideas.
Understanding the critical role of a vast network of partners is essential for maintaining a competitive edge in today’s market.
At Network Right, we specialize in Managed IT services, IT support, professional services, and vCISO services, positioning ourselves as your strategic technology partner. By meticulously identifying your specific technology needs, we can offer tailored solutions that drive your business forward and keep you ahead in your industry.
Maintaining strong partnerships is crucial for continuous innovation and growth. With Network Right, you gain access to a wealth of local expertise and a commitment to excellence that ensures your IT infrastructure is not only current but also future-proof.
Fill out the form below to initiate access to our network of 500+ software and hardware partners and meet all your business needs.

June 11, 2025
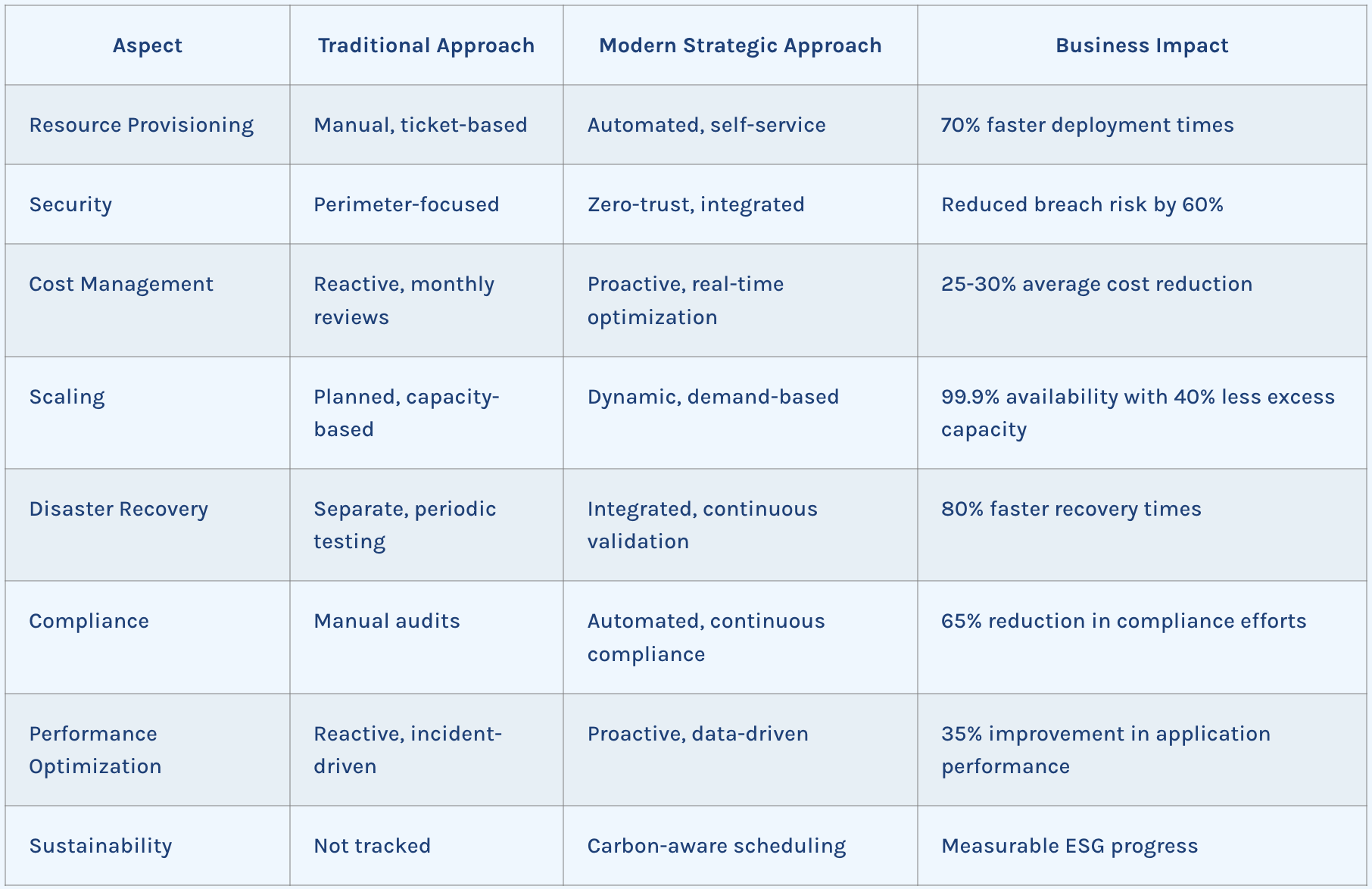
Effective cloud infrastructure management (CIM) is no longer optional; it is a prerequisite for controlling costs, safeguarding data, and delivering the always-on digital experiences that customers expect. This guide explains how forward-thinking organizations streamline complex, multi-cloud estates and turn infrastructure into a durable, competitive advantage.
Follow the frameworks below to achieve similar results—and revisit them quarterly to keep your program evergreen.
Cloud infrastructure management encompasses the oversight, administration, and optimization of all cloud computing resources—including servers, storage, networks, and services. As organizations continue their digital transformation journeys, the complexity of these environments grows exponentially.
Modern cloud infrastructure is characterized by multi-cloud and hybrid deployments, containerization, Infrastructure as Code (IaC), and emerging technologies like serverless computing. According to recent industry data, over 85% of enterprises now employ a multi-cloud strategy, with the average organization using more than five different cloud platforms.
This complexity creates both opportunities and challenges. While organizations benefit from increased flexibility and specialized services, they also face heightened security risks, compliance concerns, and potential cost overruns without proper management practices.
Successful cloud infrastructure management begins with strategic planning. This involves:
Organizations should regularly review their resource allocation strategy, ensuring it evolves alongside changing business requirements and technological advancements. For businesses looking to align their cloud infrastructure with broader organizational goals, a well-structured IT strategy drives growth and ensures technology investments deliver measurable business value.
Manual infrastructure management is increasingly untenable in today’s complex environments. Automation and IaC approaches offer significant advantages:
Tools like Terraform, AWS CloudFormation, and Ansible have become essential components of modern cloud management, enabling teams to provision and manage resources programmatically. Many organizations are also adopting GitOps practices to synchronize code repositories with deployed infrastructure, further enhancing consistency and auditability.
Cloud costs can quickly spiral without proper oversight. Effective financial management includes:
Organizations with mature cloud financial management practices can realize cost savings of 20-30% compared to those taking an ad-hoc approach. For companies lacking in-house FinOps expertise, managed IT services teams can implement cost governance frameworks quickly and effectively.
Security cannot be an afterthought in cloud infrastructure management. Leading organizations:
With regulatory requirements growing more stringent, compliance support should be integrated directly into infrastructure management processes rather than treated as a separate function. Modern approaches include “compliance-as-code” that can trigger deployment blocks when controls fail, rather than relying on retroactive audits.
Continuous monitoring and optimization are essential for maintaining high-performing cloud environments:
Modern cloud management platforms now incorporate AI-driven analytics to provide proactive recommendations for performance improvements and cost savings. For organizations with distributed teams or complex infrastructures, remote IT support can provide 24/7 monitoring and rapid intervention capabilities.
As applications become more distributed, cloud infrastructure management must extend beyond traditional cloud environments to encompass edge computing resources. This requires:
Organizations successfully integrating edge and cloud infrastructure gain competitive advantages through reduced latency, enhanced resilience, and improved data processing capabilities for real-time analytics and IoT workloads.
Artificial intelligence is transforming how organizations approach cloud infrastructure management:
As these technologies mature, they’re enabling smaller teams to manage increasingly complex environments while improving overall efficiency and reliability. For organizations looking to leverage AI capabilities within their infrastructure, an AI readiness assessment can help identify integration opportunities and establish the necessary foundations.
Zero-trust architectures are replacing traditional VPN boundaries, improving both security posture and user experience:
These approaches align perfectly with distributed workforces and modern remote managed IT services, enabling secure access regardless of user location.
Environmental considerations are becoming central to cloud strategy:
Leading organizations now include sustainability metrics alongside traditional KPIs when evaluating their cloud infrastructure effectiveness, recognizing both the corporate responsibility and potential cost benefits of efficient resource utilization.
Effective governance provides the foundation for successful cloud management:
These frameworks should balance the need for control with the agility that makes cloud computing valuable in the first place. Many organizations benefit from IT consulting to establish these governance models based on industry best practices.
Breaking down traditional silos between development and operations teams is essential:
Organizations with mature DevOps practices deploy code 46 times more frequently with significantly fewer failures compared to traditional approaches. For companies transitioning to these practices, IT infrastructure management services can accelerate the adoption process.
The rapid evolution of cloud technologies requires ongoing skills development:
Many organizations find that a combination of internal expertise and external support provides the optimal balance of specialized knowledge and business context.
Robust disaster recovery planning is non-negotiable:
Regular disaster recovery testing often reveals configuration issues or dependencies that might otherwise remain undetected until an actual outage. Organizations seeking to strengthen their business continuity should consider a thorough business impact analysis to identify and prioritize critical systems.
Comprehensive documentation supports both operational efficiency and compliance:
Organizations with strong documentation practices experience faster incident resolution and more successful infrastructure changes. For companies looking to improve their documentation practices, IT documentation done right provides a valuable framework.
To help organizations move from theory to practice, we’ve outlined a practical 12-month roadmap for cloud infrastructure management excellence:

This phased approach allows organizations to build capabilities incrementally while delivering tangible business value at each stage. For companies looking to accelerate any phase of this roadmap, customized IT solutions can provide targeted expertise and implementation support.
As cloud environments grow more complex, effective infrastructure management has become a strategic differentiator. Organizations that excel in this area not only reduce costs and minimize risks but also gain the agility needed to capitalize on new opportunities quickly.
The most successful companies treat cloud infrastructure management as an ongoing journey rather than a destination. They continuously refine their approaches, incorporate new technologies, and balance immediate operational needs with long-term strategic objectives.
By implementing the practices outlined in this article and staying attuned to emerging trends, organizations can transform their cloud infrastructure from a technical necessity into a genuine competitive advantage—enabling innovation, enhancing security, and driving sustainable growth in an increasingly digital world.
Ready to take your cloud infrastructure management to the next level? Explore Network Right’s comprehensive IT infrastructure management services or book a meeting.
.jpg)
June 10, 2025
Moving offices can be quite exciting, especially when scaling up, but it could easily become hectic and stressful if not well coordinated. Professional IT office relocation services can help make this transition smooth and efficient.
Unlike moving homes, office relocation involves more than just moving physical things; you need to guarantee that your data flows uninterrupted and systems remain secure—your whole IT infrastructure needs to be handled with care to avoid disruptions. This is where specialized IT relocation expertise becomes crucial.
How will you manage the transfer of sensitive information? How will your IT team handle potential disruptions? How will you manage IT equipment relocation safely and securely?
Tapping into expert IT guidance helps you answer these questions and navigate the waters smoothly. It also ensures you maintain productivity before, during, and after your relocation.
Let’s explore how you can avoid common pitfalls to guarantee a seamless shift for your business.
Moving offices can be quite exciting, especially when scaling up, but it could easily become hectic and stressful if not well coordinated. Professional IT office relocation services can help make this transition smooth and efficient.
Unlike moving homes, office relocation involves more than just moving physical things; you need to guarantee that your data flows uninterrupted and systems remain secure—your whole IT infrastructure needs to be handled with care to avoid disruptions. This is where specialized IT relocation expertise becomes crucial.
How will you manage the transfer of sensitive information? How will your IT team handle potential disruptions? How will you manage IT equipment relocation safely and securely?
Tapping into expert IT guidance helps you answer these questions and navigate the waters smoothly. It also ensures you maintain productivity before, during, and after your relocation.
Let’s explore how you can avoid common pitfalls to guarantee a seamless shift for your business.
Understanding your existing setup is essential for identifying what’s working well and what isn’t. Working with experienced IT infrastructure management specialists who understand IT office moves and wiring can help thoroughly assess your current systems and identify opportunities for improvement during the transition. You need to know the details of your current technology landscape to make sure nothing critical gets overlooked in the change. Evaluating the existing setup will let you identify what’s working well and what isn’t. This assessment should cover everything from hardware and software systems to data storage solutions and network configurations that your business relies on daily.
When you’re aware of the age, capacity, and performance of your current systems, you can make informed decisions about upgrades or replacements. Maybe you’ve outgrown your old servers, or perhaps your backup systems aren’t as reliable as you need them to be. Professional office relocation wiring services can help ensure your new setup meets all your current and future needs. Recognizing these factors early prevents costly downtime and compatibility issues during the relocation.
Additionally, evaluating your IT infrastructure helps you allocate resources more effectively. It’ll help you discover what needs to be packed with extra care, what can be easily transported, and what might require special handling procedures. This step isn’t just a precaution; it’s a strategic approach to safeguard your operational continuity. You don’t want to find yourself in your new office only to realize your critical data didn’t make it through the move unscathed.
“…fail to plan, plan to fail.” You need to develop a comprehensive strategy for your office relocation. Create a detailed timeline that considers all critical milestones from the initial move to the final setup in the new location.
Here are a few things to consider when planning the relocation:
Use this comprehensive checklist to ensure you’ve covered all critical IT aspects before your office relocation.
Customize this checklist based on your office size and IT infrastructure complexity. Share it with your team to ensure nothing is overlooked during the move preparation.
When do you want to move? How long should it take? What time will you start? What are the most important? It’s important to establish clear, open lines of communication early on to make sure they understand the logistics and timing of your office move. Begin by scheduling a meeting to discuss the overall timeline and any specific requirements or challenges related to your IT infrastructure. Make sure each vendor knows their role and the exact expectations you have of them.
Once timelines are sorted, you need to provide detailed information about the new office layout. This includes floor plans and network setup requirements so that all hardware and services can be appropriately planned for. What goes to what floor? Discuss access times for installations and any restrictions that might affect their work.
It’s also vital to designate a point of contact within your organization who’ll handle vendor queries and coordinate efforts. This liaison will streamline communications, reducing the likelihood of misunderstandings or delays.
Lastly, make sure you’re on the same page regarding the budget. Clear cost expectations will help avoid surprises and ensure the relocation proceeds smoothly. Keep regular tabs on progress and schedule follow-up meetings to address issues as they arise.
Testing your systems is an important step that will help mitigate potential IT issues before they arise. Working with experts who specialize in IT setup for new office environments can help ensure all systems are properly configured and tested. This will help avoid conflicts or blame games between your employees or with the vendors post-relocation. This typically involves network performance evaluation and system backup protocols.
Assessing your network’s performance before relocating guarantees that IT systems will operate efficiently in the new office space. To guarantee a seamless shift, you must thoroughly test and assess the network capabilities.
Here are key factors you should focus on:
Addressing these areas will help you avoid unexpected downtime and productivity losses post-relocation.
After guaranteeing your network’s performance is up to par, it’s vital to establish robust system backup protocols before you move. Identify all critical data across your company’s network, and make sure every piece of data is accounted for and backed up in multiple secure locations. This isn’t just about copying files; it’s about creating a thorough backup strategy that includes regular snapshots and off-site storage solutions to safeguard against data loss during transit.
You should also test these backups regularly before the move. Try restoring data from the backup to check for integrity and completeness. This step ensures you move your office and protect your business against potential data disasters.
During the relocation, you’ll need to guarantee that your IT infrastructure is systematically dismantled, transported, and reassembled with minimal downtime. This process can be complex, but with the right strategies, you’ll navigate through it smoothly.
Here are some essential steps:
Following these steps will help you manage your IT effectively and ensure your cybersecurity measures are intact, avoiding potential pitfalls and downtime.
Once your office move is complete, focus on setting up your IT systems to guarantee they’re fully operational.
After you’ve settled into your new office space, the real work begins with ongoing IT support and adjustments.
You’ll need to keep a close eye on system monitoring to catch any potential issues early. Addressing common problems quickly will guarantee that your team maintains high productivity without significant downtime.
To ensure your system’s performance remains excellent after relocating your office, you require ongoing IT support and adjustments. You’ll need to monitor and fine-tune your IT systems to guarantee they meet the new operational demands. This phase isn’t just about fixing issues as they arise; it’s about proactive improvement and optimization to prevent potential problems down the line.
Here are some key actions you should consider:
As you settle into your new office, some things might need getting used to, so you’ll likely encounter some common IT issues that require prompt and effective troubleshooting.
Network connectivity might be your first hurdle; make sure all cables are correctly connected and routers are properly configured. You might also face challenges with printer setups or email configurations. So, double-check IP addresses and DNS settings, as these often get overlooked in the chaos of a move.
If software isn’t behaving as expected, verify that all systems are updated to their latest versions. Remember, compatibility can be an issue, especially if hardware has been updated or replaced. Don’t hesitate to contact your IT support team for help. They’re there to assist you in smoothing out these initial bumps.
As you embark on your office relocation, the role of specialized IT expertise can’t be overstated. By meticulously evaluating your existing IT infrastructure and planning your move with precision, you significantly reduce potential risks and pave the way for a seamless transition. Remember, the success of your move heavily relies on strategic foresight and effective coordination with experienced vendors.
At Network Right, we understand the complexities involved in office relocations. Our comprehensive IT office relocation services ensure a smooth transition for your business. We have a team of experts in Professional IT services, IT support, and vCISO services are well-equipped to guide you through this crucial process. We’ve engaged in a comprehensive pre-move assessment and implemented robust testing phases to safeguard operational continuity. Furthermore, our post-move ongoing support ensures that your business maintains its efficiency and is well-positioned for future growth.
Contact us to get started. Let’s discuss how our localized expertise and strategic IT solutions can contribute significantly to the success of your office relocation.

June 10, 2025
Is your business still relying on physical keys that can be lost, copied, or stolen? Are you struggling to track who accesses your facilities and when? Can you instantly revoke access when an employee leaves? If these questions keep you up at night, you’re not alone.
For modern businesses, security vulnerabilities at physical entry points create real business risks—from data breaches to theft of assets and intellectual property. Modern security access systems transform how you control, monitor, and manage facility access, delivering peace of mind while reducing administrative overhead and strengthening your overall security posture.
TL;DR: Modern security access systems replace vulnerable key systems with digital credentials, providing instant access management, detailed audit logs, and integration with your broader security infrastructure. They reduce administrative costs while strengthening security and compliance posture. Leading solutions include Ubiquiti, Brivo, Kisi, and Verkada, each optimized for different business needs.
Top benefits:
The days of managing physical security with metal keys are rapidly disappearing. Traditional key-based systems create significant vulnerabilities and operational challenges that put your business at risk.
One lost master key can cost thousands in re-keying expenses and expose sensitive assets or intellectual property. Modern access control eliminates this single point of failure while providing capabilities impossible with mechanical locks.
Traditional keys present several critical limitations:
A comprehensive security access system typically consists of four main components working together to create a secure environment:
Access credentials identify authorized users through physical or digital tokens. These range from traditional access cards to mobile credentials and biometric identifiers, each offering different levels of security and convenience.
Management software ties the system together, allowing administrators to configure access rules, manage users, and monitor system activity from a centralized dashboard.
Modern access systems create multiple layers of protection that static locks simply cannot match. Every door event—successful or denied—is logged automatically, giving you a complete audit trail for compliance and security investigations.
The real-time nature of digital access control enables:
Beyond security enhancements, these systems deliver significant operational advantages that translate to measurable ROI. Remote management capabilities allow security teams to administer access from anywhere, particularly valuable for organizations with distributed facilities or hybrid work models.
Integration with other business systems creates powerful automation opportunities, including:
Organizations with comprehensive managed IT services can leverage these integrations to create seamless security workflows that enhance both protection and productivity.
When selecting a security access system provider, several leaders stand out in the market with distinct strengths:

When evaluating security access systems, look beyond initial hardware costs to consider the total lifecycle investment. While upfront expenses typically range from $300-1,200 per door depending on hardware quality and features, traditional key management carries hidden costs that often go untracked.
The ROI calculation should factor in:
Security Metric: The average lost-key incident costs $2,800 in re-keying expenses and operational downtime, not including potential losses from unauthorized access.
Before selecting a system, conduct a thorough evaluation of your physical security landscape. Document all entry points requiring protection and identify different security zones with varying access requirements. Consider how your existing security technologies will integrate with the new access system and map potential vulnerability points in your current setup.
Document a comprehensive framework defining who should have access to which areas and when. This policy should establish standardized access levels based on roles, procedures for temporary access, protocols for credential revocation, and guidelines for ongoing system management.
Proper implementation ensures your system functions correctly from day one. Working with experienced installers like Network Right’s security installation team ensures appropriate reader placement, proper network configuration, and thorough testing of all components.
User adoption is critical to security success. Develop training programs for both administrators and end-users covering system management, proper credential handling, procedures for lost credentials, and ongoing security best practices.
Modern security access systems play a crucial role in meeting regulatory requirements across multiple frameworks. For Bay Area businesses, these systems help satisfy:
Many organizations leverage professional compliance support services to ensure their security access systems are properly configured to meet these regulatory requirements.
The detailed audit logs automatically generated by these systems provide the documentation needed to demonstrate compliance during audits and assessments, significantly reducing administrative burden while improving security posture.
When deploying a new security access system, anticipate and prepare for common hurdles to ensure a smooth transition.
Network infrastructure considerations are paramount, as modern systems rely on robust connectivity. Ensure your network can support additional devices and address power requirements through properly managed IT infrastructure. Implement backup systems for network or power failures to maintain security during outages.
If replacing an existing system, develop a careful migration plan that includes:
When a San Francisco-based financial services company with 120 employees moved to a new office, they needed to upgrade from keys to a modern access control system that would meet their security requirements and compliance needs.
Network Right implemented a Verkada system that integrated with their existing security cameras, providing a unified security platform. The solution included mobile credentials, eliminating physical cards, and integrated with their HR system for automatic access provisioning and revocation.
The result: $18,000 annual savings in security administration costs, enhanced compliance documentation, and improved employee experience with seamless access across all office areas.
The security access system landscape continues to evolve with emerging technologies that enhance both security and user experience.
Mobile-first access is rapidly becoming the standard, with physical credentials giving way to smartphone-based authentication methods. These solutions leverage Bluetooth Low Energy, NFC, and mobile wallet integration to provide convenient yet secure access options that eliminate the need for physical credentials.
Artificial intelligence is transforming security through anomaly detection that identifies unusual access patterns and predictive analytics that anticipate potential security threats. These systems continuously optimize based on usage data, creating increasingly intelligent security environments.
Once implemented, your security access system requires ongoing attention to maintain optimal performance and security.
Conduct regular security audits reviewing access logs for unusual patterns, reviewing user lists for outdated permissions, and analyzing failed access attempts. These reviews help identify potential security gaps before they can be exploited.
Keep your system secure by promptly applying security patches, updating firmware on all hardware components, and upgrading software to access new features. Test all updates in controlled environments before full deployment to prevent disruptions.
A well-designed security access system provides far more than basic entry control—it becomes a critical component of your overall security strategy, protecting your people, property, and data. By carefully selecting the right system for your needs and implementing it with attention to both security and usability, you can create a safer workplace while streamlining operations.
For organizations in the Bay Area looking to implement or upgrade their security access systems, Network Right’s professional installation services provide expert guidance through the selection, implementation, and maintenance processes. Our experience with leading platforms like Ubiquiti, Brivo, Kisi, and Verkada ensures your system will be optimized for your specific security requirements while meeting California’s unique compliance landscape.
Ready to enhance your facility’s security with a modern access control system? Contact Network Right today for a consultation on the best security access system for your business needs.
Ready to meet your new IT team?
333 Bryant St #250,
San Francisco,
CA 94107
408 Broadway FL 5.
STE B, New York,
NY 10013
